When your tiny internet-connected devices just won't chat with your private cloud space, it can feel like a quiet moment of worry, a little bit like shouting into a wide, open field with no answer. You've got these clever gadgets out there, maybe gathering important information or controlling something far away, and they need to send their messages to a safe, secluded spot in the Amazon Web Services cloud. So, when that secure connection to your remote IoT devices in a VPC on AWS seems to hit a wall, it really does make you stop and think.
It's a common story, actually, for folks trying to make these distant connections work. You've set things up, you believe everything is in its proper place, and yet the data isn't flowing, or your devices aren't getting their instructions. This can be rather frustrating, a bit like trying to find your way through a winding path when the signs are all pointing in different directions. We're talking about those times when you want to securely connect remote IoT devices to your AWS VPC, and for some reason, it's just not quite doing what you want.
This article is here to help you sort through those moments when the path feels a bit unclear. We'll look at the common spots where things might get tangled, offering some simple ideas to help you figure out what's going on. It's about making sure your remote IoT connections to that private cloud area in AWS are not only working but also keeping everything safe and sound. We'll explore some ways to get your devices talking again, smoothly and without a hitch, so you can get back to what matters.
Table of Contents
- What Makes Securely Connect Remote IoT VPC AWS Tricky?
- Is Your Network Path Clear for Remote IoT VPC AWS?
- Are Your Device Identities in Order for Securely Connect Remote IoT?
- How Do You Check the AWS IoT Core Side When Securely Connecting Remote IoT?
- Checking the VPC Endpoint for Securely Connect Remote IoT
- Where to Look for Clues When Securely Connecting Remote IoT VPC AWS?
- Device Side Checks for Securely Connect Remote IoT
- Best Ways to Keep Your Remote IoT VPC AWS Connections Strong
What Makes Securely Connect Remote IoT VPC AWS Tricky?
Getting your remote IoT devices to chat securely with a private section of your AWS cloud, what we call a VPC, can sometimes feel like trying to build a very specific bridge. You have the device on one side, perhaps out in the wild, gathering bits of information, and then you have this protected space in the cloud where all that information needs to go. The challenge often comes from making sure every single part of that bridge is just right, so that messages can travel back and forth without anyone else listening in or interfering. It's almost like setting up a secret handshake for every piece of information, ensuring only the right parties are involved.
One reason things can get a bit tangled is because there are several layers of protection involved. You have the security measures on the device itself, then the way it connects to the internet, and then the careful rules set up within AWS to guard your private cloud area. Each of these layers has its own set of settings, and if just one tiny setting is out of place, the whole conversation can stop. It's very much like having a lock on a door, but the key is slightly bent, or the door frame is just a little off. You know, you try to turn the key, and it just doesn't quite catch. This is particularly true when you're trying to securely connect remote IoT devices to an AWS VPC; there are many places for a small snag to appear.
Another thing that makes this kind of setup a little challenging is the sheer distance, in a way, between the device and the cloud. These aren't devices sitting right next to your main computer; they're often far away, perhaps in a distant field or a quiet building. This means you can't just plug them in directly. They rely on the internet, and then on special connections that route them into your private cloud space. This whole setup requires careful planning, a bit like laying out a very long, very important pipeline. If there's a tiny leak or a block anywhere along that pipeline, the flow stops. So, making sure everything is aligned when you securely connect remote IoT devices to a VPC in AWS is really quite important.
Is Your Network Path Clear for Remote IoT VPC AWS?
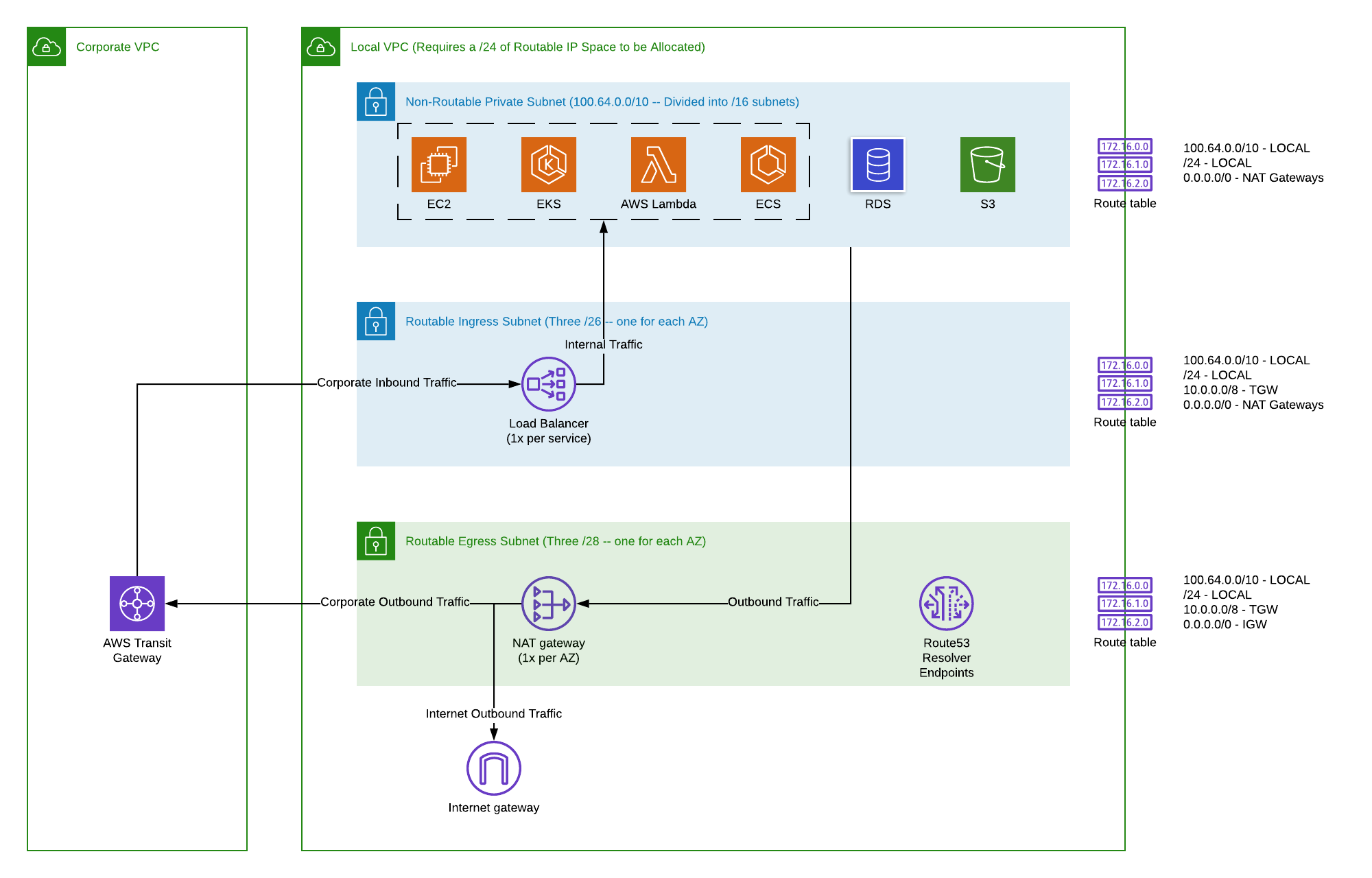
When your remote IoT devices aren't talking to your AWS VPC, one of the first places to look is the network path itself. Think of it like a road for your data. Is that road open, or are there unexpected roadblocks? Sometimes, the issue comes down to what are called "security groups" or "network access control lists," which are essentially digital bouncers at the entrance of your private cloud space. They decide who gets in and who doesn't. If your device's messages aren't on the guest list, they simply won't get through. You know, it's a bit like having a party, and your friend shows up, but their name isn't on the list at the door. So, making sure these bouncers are letting the right traffic through is a big part of getting your remote IoT connections working with your AWS VPC.
Then there are the "route tables," which are like maps for your data. They tell your messages which way to go to reach their destination inside your AWS VPC. If the map has a wrong turn, or if a path is missing, your data might just wander off into the digital wilderness. It's surprisingly common for a small error in these maps to cause a big problem. You might have set up a special connection, like a VPC endpoint, but the route table isn't pointing traffic towards it correctly. This is actually a key area to check when you're trying to securely connect remote IoT devices to your AWS VPC and finding it's not quite working.
Also, consider the "network address translation," or NAT, setup. Sometimes, your devices might be using private addresses that need to be translated into public ones to get out onto the internet, and then translated back to private ones to get into your VPC. If this translation service isn't set up correctly, or if it's having trouble, your messages might get lost in translation. It's almost like trying to talk to someone who speaks a different language, but your translator isn't there. So, checking these network elements is a really good first step to help your remote IoT devices connect to your AWS VPC.
Are Your Device Identities in Order for Securely Connect Remote IoT?
Beyond the network roads, a big part of getting your remote IoT devices to talk to your AWS VPC involves their identities. Each device needs a proper way to prove it is who it says it is, and that it has permission to send and receive messages. This usually involves digital certificates, which are like tiny, very secure passports. If a device's passport is expired, or if it's not signed by the right authority, or if the device itself doesn't have the correct password, it won't be allowed into your private cloud space. You know, it's a little like showing up at an airport with an old passport; you just won't get on the plane. This is a very common place for issues to pop up when you're trying to securely connect remote IoT devices.
Along with these digital passports, there are also "policies" attached to each device's identity. These policies are like a set of rules that say exactly what a device is allowed to do. For instance, a policy might say this device can only send messages to a specific topic, or it can only receive commands from a certain place. If the policy doesn't grant the necessary permissions for your device to interact with your AWS VPC, then even with a valid passport, the device won't be able to do what you want. It's almost like having a ticket to a concert, but your ticket only lets you into the lobby, not the main hall. So, checking these policies is pretty important for getting your remote IoT devices to work properly.
Sometimes, the issue isn't with the passport or the rules themselves, but with how the device is trying to use them. The device might have the right certificate and policy, but its internal settings for connecting to AWS IoT Core are a bit off. Maybe the endpoint address it's trying to reach is wrong, or the way it's presenting its credentials isn't quite right. This is where the actual software running on your device comes into play. It's very much like having the right key, but trying to put it into the wrong lock. So, taking a look at the device's own setup for how it tries to securely connect remote IoT elements is a worthwhile step.
How Do You Check the AWS IoT Core Side When Securely Connecting Remote IoT?
When your remote IoT devices are having trouble reaching your AWS VPC, a good place to investigate is the AWS IoT Core service itself. This is the central hub where all your devices are supposed to register and communicate. Think of IoT Core as the reception desk for all your internet-connected gadgets. If something isn't quite right at the reception desk, then even if your devices are perfectly fine and your network path is clear, they won't be able to get their messages through to your private cloud area. So, checking the settings and status within AWS IoT Core is pretty essential for a smooth connection. It's almost like making sure the front office knows you're coming and has a spot ready for you.
One key thing to check here is the "endpoint" your devices are trying to reach. AWS IoT Core provides specific addresses for devices to connect to, and if your device is trying to talk to an old, incorrect, or public endpoint when it should be using a private one within your VPC, then that's a definite problem. It's like trying to mail a letter to an old address; it just won't get to the right place. You know, sometimes people forget to update these details when they change their setup, and it can cause a real headache. So, verifying that your remote IoT devices are aiming for the correct private endpoint in AWS IoT Core is a very important step for a secure connection.
Another area to look at is the "thing" registration and its associated policies within AWS IoT Core. Each of your remote IoT devices should be registered as a "thing," and each "thing" needs a set of permissions that allows it to interact with the rest of your AWS environment, including your VPC. If these permissions are too restrictive, or if the "thing" isn't properly linked to the right certificates and policies, then it won't be able to communicate. It's basically like having a VIP pass, but the bouncer at the door doesn't recognize it. So, ensuring these details are all squared away in AWS IoT Core is a big part of getting your remote IoT devices to securely connect to your AWS VPC.
Checking the VPC Endpoint for Securely Connect Remote IoT
A specific and very important piece of the puzzle when you're trying to securely connect remote IoT devices to your AWS VPC is the VPC endpoint itself. This endpoint acts like a direct, private tunnel from your private cloud space to AWS services like IoT Core, without ever having to go out onto the public internet. If this tunnel isn't built right, or if there's a block inside it, then your devices won't be able to reach IoT Core privately. You know, it's kind of like having a secret passage, but the door at one end is stuck. This is a common point of failure when trying to establish a private connection.
There are a couple of types of these tunnels, too. You might have an "interface endpoint" or a "gateway endpoint." For IoT Core, you'll typically be looking at an interface endpoint. It's important to make sure that this specific type of endpoint is configured correctly for the IoT Core service. If you've chosen the wrong kind, or if the settings within the endpoint itself are not allowing the right traffic, then your remote IoT devices won't be able to use that private path to your AWS VPC. It's very much like having a special road built, but it's only for trucks, and you're trying to drive a car on it.
Beyond the type, you also need to check the "security groups" associated with your VPC endpoint. Just like other parts of your network, these endpoints have their own bouncers. They need to be set up to allow incoming connections from your private network and outgoing connections to the IoT Core service. If these security group rules are too tight, or if they're missing, then the private tunnel will effectively be closed off. So, making sure the VPC endpoint is properly configured, with the right type and the correct security rules, is a big piece of the solution for getting your remote IoT devices to securely connect to your AWS VPC.
Where to Look for Clues When Securely Connecting Remote IoT VPC AWS?
When you're trying to figure out why your remote IoT devices aren't talking to your AWS VPC, knowing where to find clues is almost as important as knowing the solution itself. AWS provides several ways to peek behind the scenes and see what's happening with your network traffic and device communications. Think of these as different windows into the inner workings of your cloud setup. If you know which window to look through, you can often spot the exact moment where things go wrong. It's very much like being a detective, gathering bits of information to piece together the whole story.
One of the most useful places to gather hints is within AWS CloudWatch. This service collects logs and metrics from almost everything happening in your AWS account. You can set up CloudWatch to gather logs from your IoT Core interactions, from your VPC flow logs (which show all the traffic going in and out of your private cloud area), and even from your Lambda functions if they're part of your setup. Looking through these logs can show you error messages, connection attempts that failed, or even just a lack of activity where you expect it. You know, sometimes the logs will just scream the answer at you, if you know how to read them. So, spending some time in CloudWatch is a really good idea when you're trying to securely connect remote IoT devices to your AWS VPC.
Another helpful spot is the "VPC Flow Logs" specifically. These logs record every single network connection attempt within your VPC, showing you the source and destination of traffic, whether it was accepted or rejected, and why. If your remote IoT device is trying to connect to your VPC endpoint, but the connection is being rejected by a security group or a network access control list, the flow logs will tell you. It's a bit like having a detailed record of every car that tried to enter or leave your private driveway, noting if they were allowed in or turned away. This is actually a powerful tool for diagnosing network-related issues when you're trying to securely connect remote IoT devices to your AWS VPC.
Device Side Checks for Securely Connect Remote IoT
While a lot of the focus is often on the cloud side, it's really important not to forget about the remote IoT device itself when things aren't working with your AWS VPC. The device is the starting point for all communication, and if it's not set up correctly, or if it's having its own issues, then no amount of perfect cloud configuration will help. Think of it like trying to make a phone call: if your phone isn't charged or doesn't have service, it doesn't matter how good the network on the other end is. So, taking a close look at the device's local settings and its ability to connect to the internet is a necessary step for a secure connection.
First, check the device's basic internet connection. Is it online? Can it reach any public website? Sometimes, the simplest issues are the hardest to spot. If the device can't even get out onto the wider internet, it certainly won't be able to reach AWS. This is a bit like checking if your car has gas before blaming the engine. You know, it's the very first thing you should confirm. Then, look at the device's internal configuration for connecting to AWS IoT Core. Is it using the correct endpoint address? Are the certificates and private keys stored correctly on the device and being used properly by its software? These are the digital credentials your device uses, and if they're off, the connection won't happen.
Also, consider the device's time. This might sound strange, but many secure communication protocols rely on accurate time synchronization. If your device's clock is significantly off from the server's clock, the security handshakes can fail. It's almost like trying to meet someone at a specific time, but your watch is an hour slow; you'll just miss them. Finally, check the device's own internal logs. Just like AWS CloudWatch, your device's software might be recording error messages or failed connection attempts. These local logs can provide valuable insights into why it's struggling to securely connect to your AWS VPC. So, don't overlook the device itself in your troubleshooting efforts.
Best Ways to Keep Your Remote IoT VPC AWS Connections Strong
Once you've got your remote IoT devices happily chatting with your AWS VPC, the goal is to keep those connections strong and reliable. It's not just about fixing problems when they pop up, but also about setting things up in a way that prevents them from happening in the first place. Think of it like building a sturdy house; you want it to stand up to the weather, not just patch it up after a storm. So, adopting some good habits and practices will help ensure your secure connections remain solid over time. You know, it's a bit like regular maintenance on a car; it keeps everything running smoothly.
One very good practice is to use "least privilege" for your device policies. This means giving your remote IoT devices only the exact permissions they need to do their job, and nothing more. If a device only needs to send data to one specific topic, its policy should reflect that. This limits the potential damage if a device were ever compromised. It's almost like giving someone a key only to the room they need to enter, not the whole building. This makes your overall setup much safer when you're trying to securely connect remote IoT elements to your AWS VPC.
Another helpful approach is to set up good monitoring and alerts. Don't wait for things to break completely before you notice. Use AWS CloudWatch to keep an eye on connection attempts, data flow, and any error messages from your IoT Core or VPC endpoints. You can set up alarms that notify you if certain thresholds are crossed, or if connection attempts start failing. This allows you to catch small issues before they become big problems. It's very much like having a smoke detector in your house; it tells you about trouble early. So, proactive monitoring is a key way to keep your remote IoT connections with your AWS VPC in good shape.
Finally, always keep your device software and certificates updated. Just like any other piece of technology, the software on your remote IoT devices might have bugs that get fixed, or security improvements that are released. Similarly, digital certificates have expiration dates, and you need to renew them before they run out. Staying current with these updates helps ensure your devices are using the latest security measures and can continue to connect without interruption. You know, it's like keeping your car's registration current; it's a small thing that prevents big headaches. So, regular updates are pretty important for keeping your remote IoT devices securely connected to your AWS VPC.
This article has covered some common reasons why your remote IoT devices might not be connecting to your AWS VPC as expected, from checking network paths and device identities to looking at AWS IoT Core and VPC endpoint settings. We've also touched on the importance of checking device-side configurations and using
Related Resources:


Detail Author:
- Name : Lela Kovacek
- Username : bianka55
- Email : pwehner@gmail.com
- Birthdate : 1979-12-18
- Address : 8691 Thompson Valley Apt. 591 Quitzonmouth, VT 29766
- Phone : 231.797.1234
- Company : Corwin-Buckridge
- Job : Milling Machine Operator
- Bio : Excepturi labore blanditiis magni sunt sapiente ut. Recusandae alias est asperiores enim sed excepturi. Voluptas praesentium rerum illum velit ab.
Socials
twitter:
- url : https://twitter.com/knitzsche
- username : knitzsche
- bio : Dolorum aut exercitationem rerum provident rerum deserunt natus. Dignissimos ratione qui doloribus in molestiae perspiciatis consequatur quis.
- followers : 3330
- following : 700
linkedin:
- url : https://linkedin.com/in/nitzsche1978
- username : nitzsche1978
- bio : Praesentium odio et est aut quod.
- followers : 679
- following : 802
tiktok:
- url : https://tiktok.com/@kevin_id
- username : kevin_id
- bio : Velit velit labore recusandae praesentium.
- followers : 370
- following : 2303